The data breach, which has affected the group ransomware Accounts, seen from the inside.
I wrote today on CyberSecurity360 what happened to the group of ransomware Accounts, as a result of their position in reference to the crisis in ukraine, siding, as expected, in support of the Russian government.
A member of the group, Ukrainian, he wanted to distinguish, while turning against the group itself, exposing through a Twitter account, a series of internal files and reserved of the group. Private conversations from the Jabber server of the cyber gang, and important technical information on their operations.
Another leak during the war in the Ukraine, in the group of ransomware is Trickbot Leak.
The contents of the leak of Accounts ransomware
In this post, the purpose is to make known the content of these leaks. I set up an account dedicated to file sharing, and I will keep, making it available below, the content of what is being leaked.
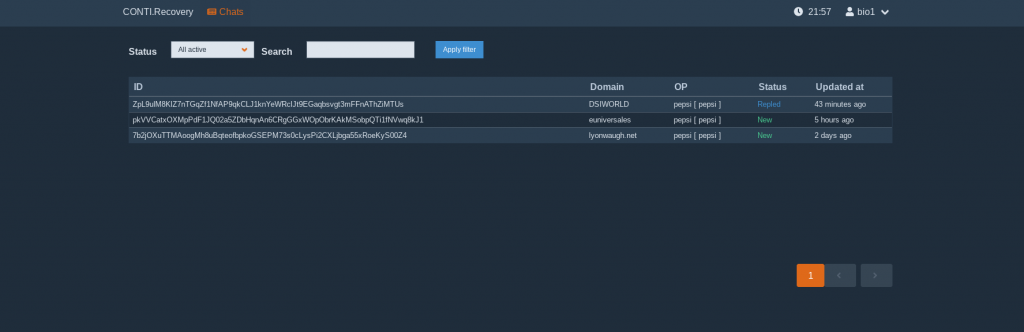
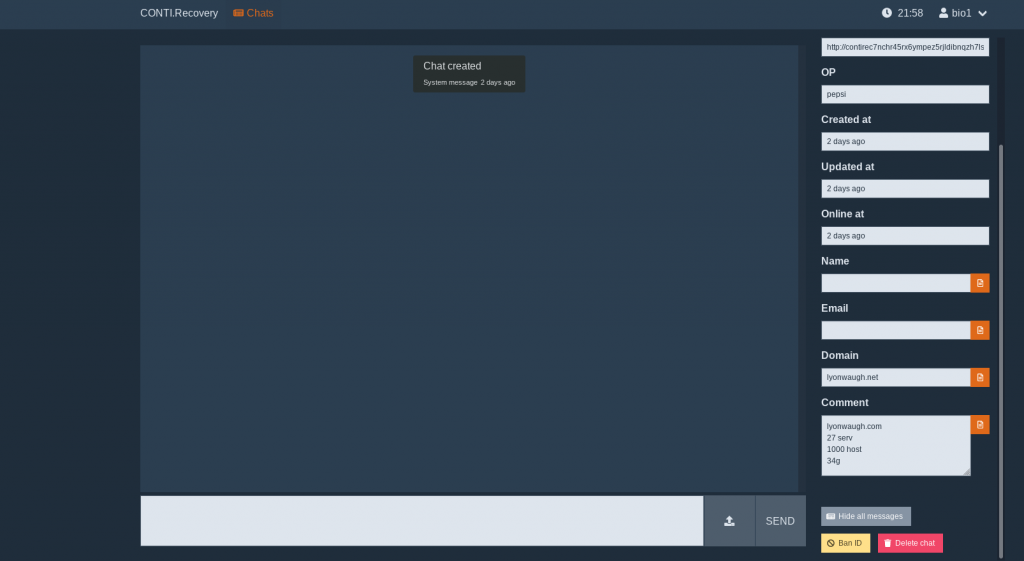


In the gallery you can find the screenshots, but this is not the only. All other files are shared here. And inside you can also find the code of the locker-v2inside the source code of the decryptor.
The rest of the files leaked
The other files, that are not screenshots, they will be inserted as said, within this shared folder. There are no passwords for the extraction of the archives, the net of those listed below.
Share Dir: ufile.I/f/yredk
- File: conti_locker_v2_zip Password: xxx (unknown yet, however, in the dir there is the code noLocker without the password, plus I added the new file conti_locker_unlock.zip containing the data of the original, but no password. Then the source code is available from the latter).
Update 20/03/22: Accounts v3
File: conti_v3.7z – Password: ВсеБудеУкраїна – the update includes the insertion in the folder of the latest version of the source code of the ransomware Accounts for the single download the link here. Instead, for the analysis of VirusTotalthis is the reference. Source Zer0DayLabbut I know that VX-Underground exposes the files in the archive, malware, without, however, the revelation of the password, useful for the extraction.
In this regard, I note that the focus in the consultation should be maximum because by extracting with this password, of course, all files are accessible on your computer. Between the source code file, there are both the encryptor and the decryptor already compiled.exe), definitely dangerous for a use not responsible for it.
Conversations Accounts ransomware
For the monitoring of the files leaked regarding the log of conversations, chat, Jabber server, etc, predispongo folders on our GitHub repository. Text files and JSON, you can find them from this directory.
https://github.com/nuke86/inSicDig-data/tree/main/Leaks/Conti
Translation in English
A user volunteer, he has shared online translation of the logs of the conversations JSON leaked, and the link to this project on GitHub, has been updated, so now you can find the folder original with the file in Russian and the folder EN with the translated files from the user.
Updates
02/03/2022: Added the file to the root Dir (conti_locker_unlock.zip) containing conti_locker_v2.zipwithout password. The source code of the locker Conti ransomware. Download Here.
02/03/2022: Added JSON translation logs in English.
01/03/2022The group Accounts continued to lose data in direct. The member contrary to their policy, pro-Russia, continues to do damage, yet having access to their infrastructure. Has not been identified, or the branching is now untraceable. I think that the heart of this group, you can only go forward with the rebrand.











