The compromise of a server within the Accounts and the data of the famous operation Accounts Leak, have allowed us to draw the links that persisted between the gang and Karakurt, group racketeering by close links with Accounts
Researchers ArticWolf were able to penetrate a server of attack used by the criminal gang informatics Accounts and have discovered several details about his attacks. In addition, it was discovered a close connection between the ransomware Accounts/the Devil and the group that specialized in extortion of data Karakurt, indicating that these groups may have been part of the same operation.
The discovery of the infrastructure of attack
The researchersas detailed in the analysis disclosed, were able to access a server Accounts, VPS inside, with the credentials of a user, presumably the leader of the criminal enterprise computer science. This has led to several revelations about his connection with the other groups.
- Researchers had hacked the account ProtonMail of the attacker and discovered the credentials of access requests, which have been used to access the server Accounts in VPS.
- The server contained more than 20 TB of data that Accounts has stolen his victims before crittografarne data.
- The server is hosted by Inferno Solutions, a provider in Russia, which supports anonymous payment methods and to accept orders connections via TOR and VPN.
An analysis of the details saved on the storage server revealed that the Accounts had data with a time stamp older belonging to the victims is still not disclosed, and who, moreover, in the course of the operation, the researchers returned to their victims.
A connection between the two groups
In addition, the researchers were able to identify, as reported by Bleeping Computer, a number of factors that indicate some association with the group Karakurt.
- A connection has been made to the IP address 209[.]222[.]98[.]19, the space in which the group of extortion Karakurt hosted his site and has published the data stolen from victims who have refused the payment. I remember at the time all of the known landmarks (all sites of the group, and data leak sites) of Karakurt appear to be down, it does not reach.
- Different wallet Karakurt have sent criptovalute to wallet evidently managed Accounts, now known to the middle of the ContiLeak of the end of February 2022. In addition, the addresses of the payment of the victims of Karakurt hosted by the wallets Accounts, they are a detail in itself definitely relevant for could expect to see a close connection.
- In addition, a victim had previously paid Accounts to unlock their data. Then, that particular client has been compromised by Karakurt through the backdoor of the Cobalt Strike left by Accounts: team games that make you think of a dialogue between the parties involved.
The response of Accounts analysts
The group of ransomware are currently the most popular in the cyber world, has not taken a good degree, this detailed analysis carried out by the analysts to ArticWolf, that in fact, as soon as it is divulged, you are seen threatened publicly by the criminal group the same. In effect, the operating rules of the Accounts, there is a rule that the group always seems to be mandatory: do not disclose details about the negotiations that the gang carries on with the victims, including chat, or screen them.
In the research to this point has been for obvious reasons, not respected, and Accounts on its website and has publicly disseminated a press release by directly contacting the company ArticWolf
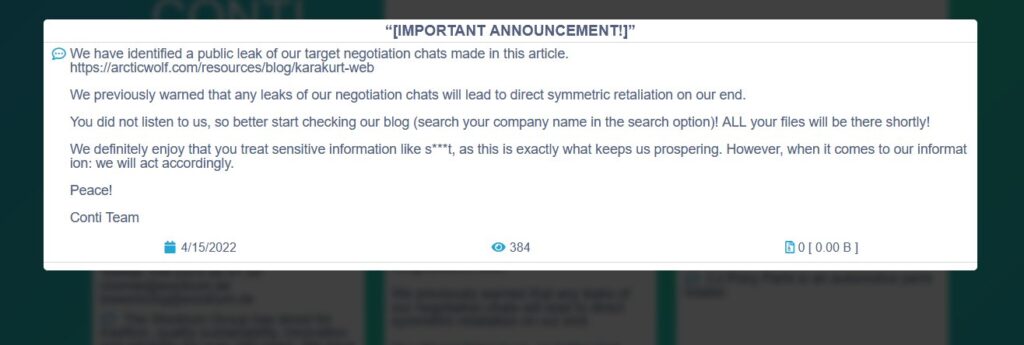
The theme of the threat is the one that refers to the leaders of the company, keep your eyes open on the next business Accounts, so as to find its internal files leaked, presumably on their web pages, notes.
I note that, in the event no longer be accessible to the content of the official search, as mentioned in the link mentioned above, the researcher Claudio it has filed a copy, of which I leave tracks here.
The devil: another link?
The researchers also found that the operators of Karakurt and the Devil share a common infrastructure.
- The analysis of the blockchain has revealed the connections of the Devil with Karakurt, and Accounts.
- One of the addresses of extortion used during an attack by the Devil contained the addresses that are used during the attacks ransomware Accounts, indicating that the group is not necessarily managed by the same attackers that manage Accounts and Karakurt.
It is evident that Karakurt and the Devil are subgroups or extensions Accounts to monetize attacks encryption with the negotiations failed. Moreover, the Accounts became large enough to expand its operations to cyber-crime. Therefore, it is suspected that the Accounts may attempt to extend its scope to develop more connections and gaining the support of other groups, that they might join up again with the Accounts and carry out targeted attacks to the victims already compromised, or even compromised (in spite of the initial attack).
In team games, restricted or extended, organized crime is never a pretty thing, and also in computer science.









